Cisco 500-220 Real Exam Questions
The questions for 500-220 were last updated at Jul 11,2025.
- Exam Code: 500-220
- Exam Name: Engineering Cisco Meraki Solutions v1.0
- Certification Provider: Cisco
- Latest update: Jul 11,2025
What are two ways peers interact with ports that Auto VPN uses? (Choose two.)
- A . For IPsec tunneling, peers use high UDP ports within the 32768 to 61000 range.
- B . Peers contact the VPN registry at UDP port 9350.
- C . For IPsec tunneling, peers use high TCP ports within the 32768 to 61000 range.
- D . Peers contact the VPN registry at TCP port 9350.
- E . For IPsec tunneling, peers use UDP ports 500 and 4500.
BE
Explanation:
In a Meraki Auto VPN setup, peers interact using the following ports:
Peers contact the VPN registry at UDP port 9350.
The VPN registry is a Meraki cloud service that helps with the establishment of VPN tunnels between Meraki devices. Peers use UDP port 9350 to communicate with this service.
For IPsec tunneling, peers use UDP ports 500 and 4500.
These ports are standard for IPsec VPNs. Port 500 is used for the initial key exchange and negotiation, while port 4500 is used for NAT traversal.
Refer to the exhibit.
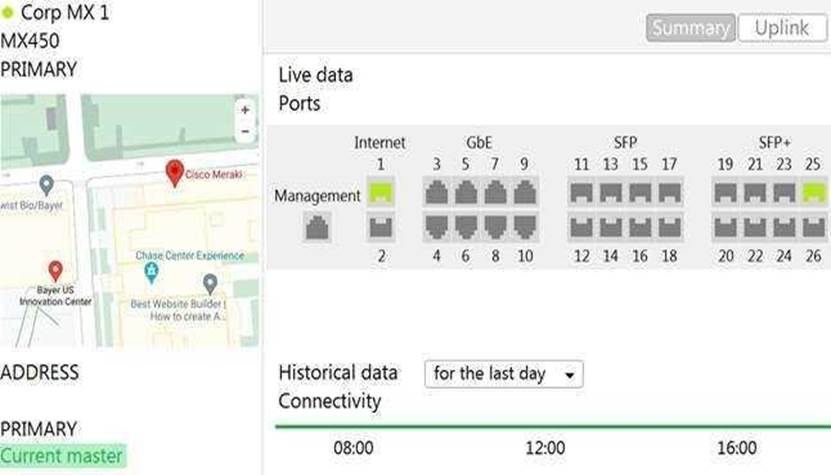
The VPN concentrator is experiencing issues.
Which action should be taken to ensure a stable environment?
- A . Add a deny any/any firewall rule to the end of the firewall rules.
- B . Remove the connection from Internet 1.
- C . Physically disconnect all LAN ports.
- D . Configure the MX appliance to Routed mode on the Addressing & VLANS page.
D
Explanation:
To ensure a stable environment for a VPN concentrator that is experiencing issues, the action that should be taken is:
Configure the MX appliance to Routed mode on the Addressing & VLANS page.
Configuring the MX to Routed mode allows it to act as a router, handling NAT and DHCP, among other functions, which can improve the stability of VPN connections. This mode is commonly used for VPN concentrators.
When an SSID is configured with Sign-On Splash page enabled, which two settings must be configured for unauthenticated clients to have full network access and not be allow listed? (Choose two.)
- A . Controller disconnection behavior
- B . Captive Portal strength
- C . Simultaneous logins
- D . Firewall & traffic shaping
- E . RADIUS for splash page settings
AD
Explanation:
When configuring an SSID with a Sign-On Splash page, to ensure that unauthenticated clients do not have full network access and are not added to the allow list (also known as a whitelist), you would need to adjust settings that relate to client access and network security post-authentication. The two settings that are relevant in this context are:
Controller disconnection behavior
This setting determines what happens if the connection between the access point and the controller (in this case, the Meraki cloud) is lost. If set to restrict access, unauthenticated clients would not be able to access the network if the AP cannot verify their status with the controller.
Firewall & traffic shaping
By configuring firewall and traffic shaping rules, you can restrict network access for unauthenticated clients. Even if they bypass the splash page, they wouldn’t be able to access the network fully without proper authentication if the rules are set to block or limit traffic.
Refer to the exhibit.
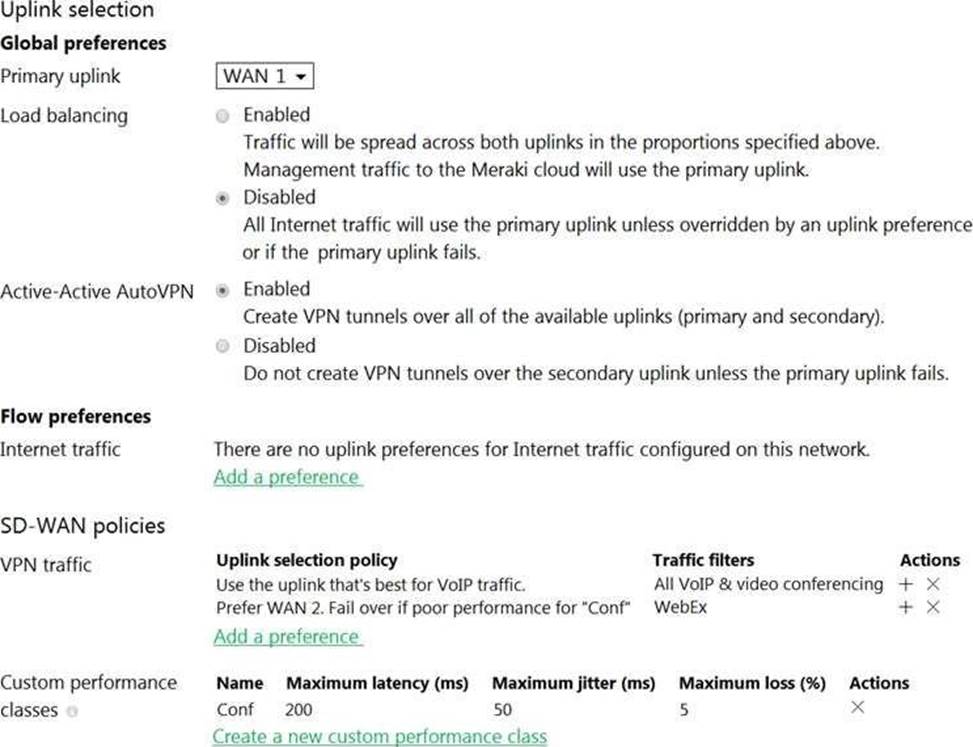
Assuming this MX has established a full tunnel with its VPN peer, how will the MX route the WebEx traffic?
- A . WebEx traffic will prefer WAN 2 as long as it meets the thresholds in the “Conf” performance class.
- B . WebEx traffic will prefer WAN 1 as it is the primary uplink.
- C . WebEx traffic will prefer WAN 2 as long as it is up.
- D . WebEx traffic will be load-balanced between both active WAN links.
A
Explanation:
Assuming this MX has established a full tunnel with its VPN peer, the MX will route the WebEx traffic based on the SD-WAN policy configured in the exhibit. The SD-WAN policy has two performance classes: Conf and Default. The Conf performance class matches the traffic with destination port 9000, which is used by WebEx for VoIP and video RTP3. The Conf performance class has a preferred uplink of WAN 2 and a failover uplink of WAN 1. It also has thresholds for latency, jitter, and loss that determine when to switch from the preferred uplink to the failover uplink. Therefore, the WebEx traffic will prefer WAN 2 as long as it meets the thresholds in the Conf performance class. If WAN 2 exceeds the thresholds or goes down, the WebEx traffic will switch to WAN 1 as the failover uplink.
For which two reasons can an organization become “Out of License”? (Choose two.)
- A . licenses that are in the wrong network
- B . more hardware devices than device licenses
- C . expired device license
- D . licenses that do not match the serial numbers in the organization
- E . MR licenses that do not match the MR models in the organization
BC
Explanation:
More hardware devices than device licenses: An organization needs to have enough device licenses to cover all the hardware devices in its network. A device license is consumed by each device that is added to the network. If the number of devices exceeds the number of licenses, the organization will be out of license and will lose access to some features and support until it purchases more licenses or removes some devices4.
Expired device license: A device license has an expiration date that depends on the license term purchased by the organization. If a device license expires, it will no longer be valid and will not count towards the license limit. The organization will need to renew the expired license or purchase a new one to avoid being out of license4.
Reference: https://documentation.meraki.com/General_Administration/Licensing/Meraki_Licensing_FAQs
Refer to the exhibit.
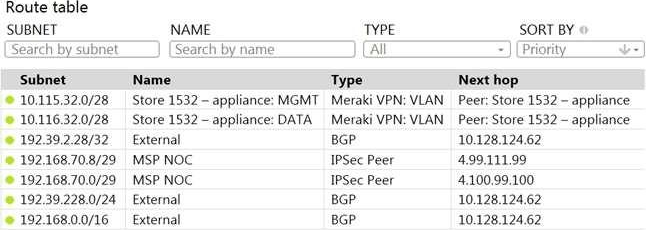
A packet arrives on the VPN concentrator with source IP 10.168.70.3 and destined for IP 10.116.32.4.
What is the next hop for the packet, based on this concentrator routing table?
- A . The concentrator gateway (10.128.124.62) is the next hop.
- B . Not enough detail is available to determine the next hop.
- C . The packet is stopped.
- D . The Auto VPN peer “Store 1532 C appliance” is the next hop.
D
Explanation:
This can be determined by looking at the concentrator routing table and finding the entry for the destination IP 10.116.32.4. The next hop for this entry is the Auto VPN peer “Store 1532 C appliance”. This question is related to the topic of Implementing Dynamic Routing Protocols in the Engineering Cisco Meraki Solutions (ECMS) official training documentation. You can find more information about this topic in the ECMS v2.2 Course Overview or the ECMS1 v2.1 Course Overview.
Refer to the exhibit.
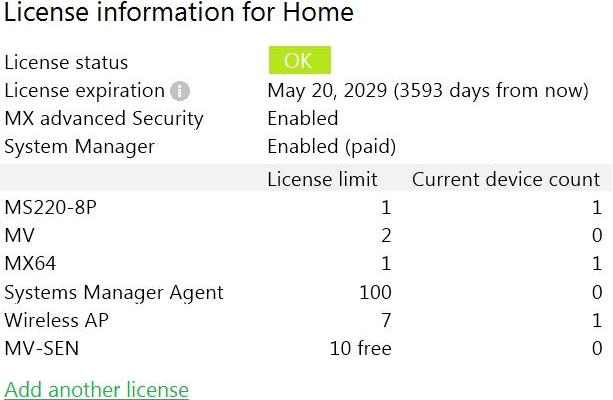
This Dashboard organization uses Co-Termination licensing model.
What happens when an additional seven APs are claimed on this network without adding licenses?
- A . All APs immediately stop functioning.
- B . All network devices stop functioning in 30 days.
- C . One AP Immediately stops functioning.
- D . All APs stop functioning in 30 days.
D
Explanation:
In the Co-Termination licensing model used by Cisco Meraki, if additional devices are added to the network without the necessary licenses, the organization is given a grace period to rectify the situation. The entire network does not immediately cease to function. Instead, the organization will have a certain amount of time to come into compliance by purchasing the required number of additional licenses. If this is not done within the grace period, the network may become non-compliant, and services may be disrupted.
Given the options:
All APs stop functioning in 30 days.
This is the most likely outcome, as the Meraki Dashboard typically provides a 30-day grace period to resolve licensing deficits before enforcing service restrictions on the network devices. During this period, the organization is expected to purchase sufficient licenses to cover the newly claimed APs. If the licensing issue is not resolved within the grace period, then the APs could be at risk of being shut down until the issue is resolved.
Which two Systems Manager Live tools are available only for Apple Macs and Windows PCs and cannot be used on iOS or Android mobile devices? (Choose two.)
- A . OS updates
- B . Send notification
- C . Selective wipe
- D . Screenshot
- E . Remote Desktop
DE
Explanation:
https://documentation.meraki.com/SM/Monitoring_and_Reporting/MDM_Commands_in_Systems_Manager – Under Live Tools Selective Wiping is only for MacOS. Here we have Windows Laptop as well
Reference: https://documentation.meraki.com/SM/Other_Topics/Systems_Manager_FAQ
